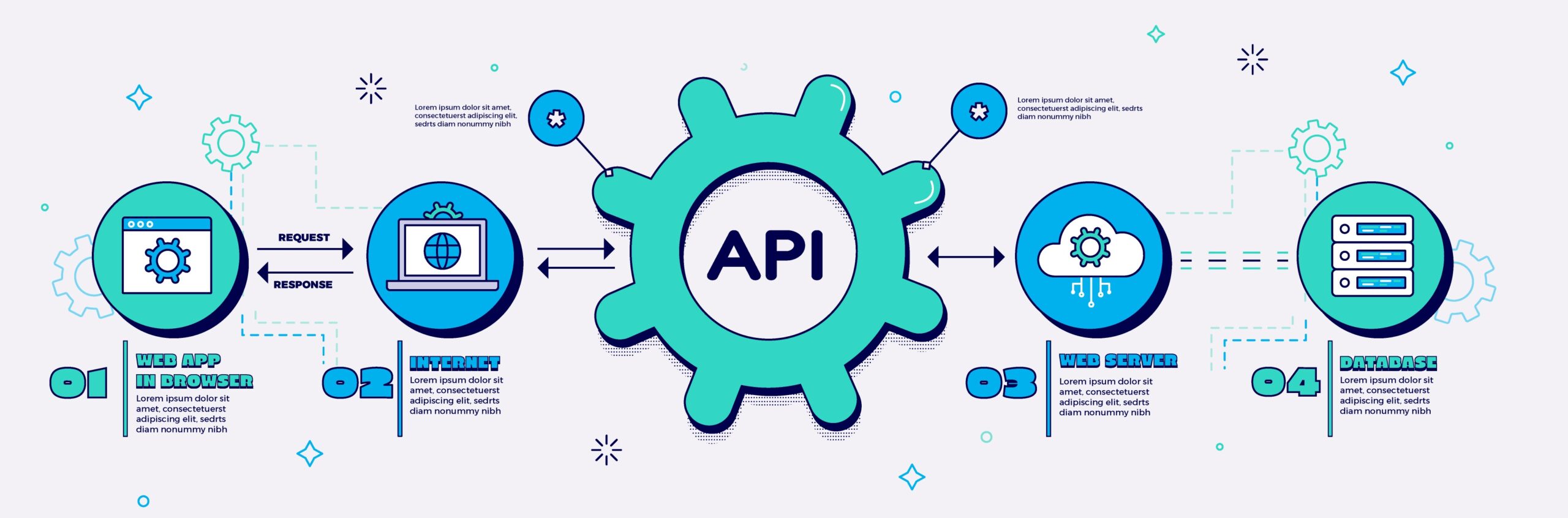
Application Programming Interface
Penetration Testing (APIPT)
Elevate Your API Security Beyond Conventional Testing
In today’s interconnected digital landscape, APIs are critical to seamless operations and data exchanges. Our API Penetration Testing service provides a meticulous evaluation to identify and address vulnerabilities, ensuring your APIs are robust against advanced cyber threats.
Why Choose Our API Penetration Testing?
While many services offer standard vulnerability assessments, our approach sets us apart. We integrate real-time threat intelligence, allowing us to identify and mitigate newly discovered vulnerabilities and sophisticated attack methods that conventional tests might miss. We thoroughly examine complex API architectures, including intricate integrations and microservices, ensuring comprehensive coverage.
Our service goes beyond basic testing by incorporating continuous monitoring to address configuration drift and adapt to evolving threats. We perform holistic risk assessments that address both technical vulnerabilities and non-technical issues, such as misconfigurations and improper API usage. Advanced attack simulations replicate real-world, multi-layered threats, uncovering subtle vulnerabilities that traditional methods may overlook.
Moreover, our approach evolves with emerging technologies, ensuring that your API security strategy remains current and effective. We offer ongoing expert support, providing continuous guidance and actionable insights to help you navigate new threats and strengthen your API defenses.
Our service goes beyond basic testing by incorporating continuous monitoring to address configuration drift and adapt to evolving threats. We perform holistic risk assessments that address both technical vulnerabilities and non-technical issues, such as misconfigurations and improper API usage. Advanced attack simulations replicate real-world, multi-layered threats, uncovering subtle vulnerabilities that traditional methods may overlook.
Moreover, our approach evolves with emerging technologies, ensuring that your API security strategy remains current and effective. We offer ongoing expert support, providing continuous guidance and actionable insights to help you navigate new threats and strengthen your API defenses.
Key Challenges
- Emerging Threats: Standard assessments may not cover newly discovered vulnerabilities or sophisticated attack techniques.
- Complex Architectures: Many tests overlook the intricacies of modern API integrations, leaving potential risks unexamined.
- Configuration Changes: Regular tests might not detect vulnerabilities introduced by ongoing configuration updates.
- Limited Simulation: Basic methods may not replicate advanced or multi-layered attack scenarios effectively.
Our Unique Solution
We address these challenges with a comprehensive approach that goes beyond traditional testing. By integrating real-time threat intelligence, we proactively identify and mitigate newly discovered vulnerabilities. Our thorough analysis covers complex API architectures and continuous monitoring ensures that configuration changes and evolving threats are promptly addressed. We perform advanced attack simulations to replicate sophisticated real-world scenarios, revealing subtle vulnerabilities often missed by conventional methods.
Our service not only uncovers critical weaknesses but also provides actionable insights and ongoing support to strengthen your API security continuously.
Our service not only uncovers critical weaknesses but also provides actionable insights and ongoing support to strengthen your API security continuously.
